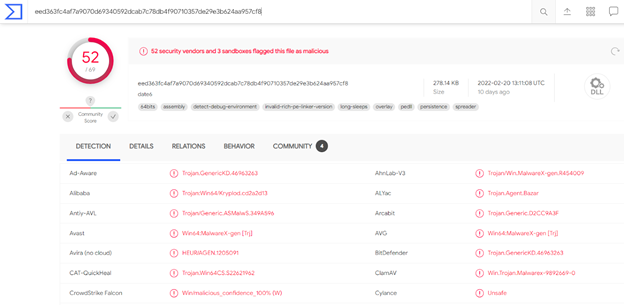
Sha256: 129569554b67a7be192a1a2bc5986337695b7676e347bb48473da4754ef479d7 - AlienVault - Open Threat Exchange

Security Onion - Linux Distro For Intrusion Detection, Network Security Monitoring, And Log Management
Malware analysis http://redmoscow.info/tmp/zzz.exe Malicious activity | ANY.RUN - Malware Sandbox Online

Meisam Eslahi, Ph.D. on LinkedIn: #cybermeisam #cybersecurity #threathunting #threatdetection… | 13 comments

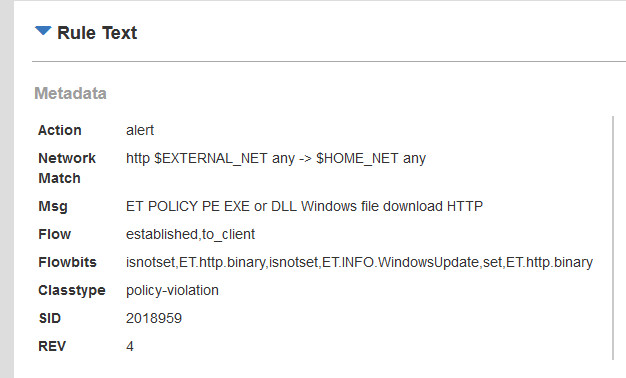
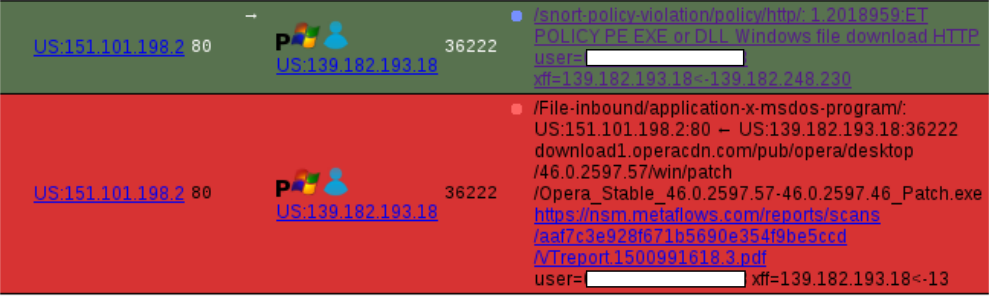
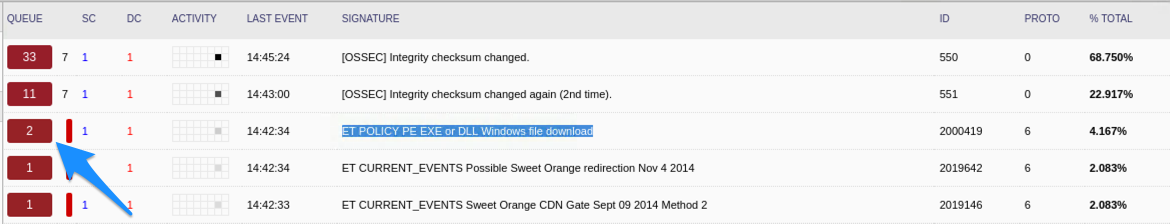
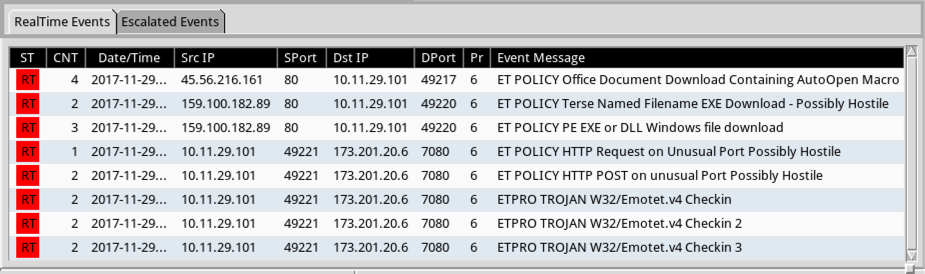
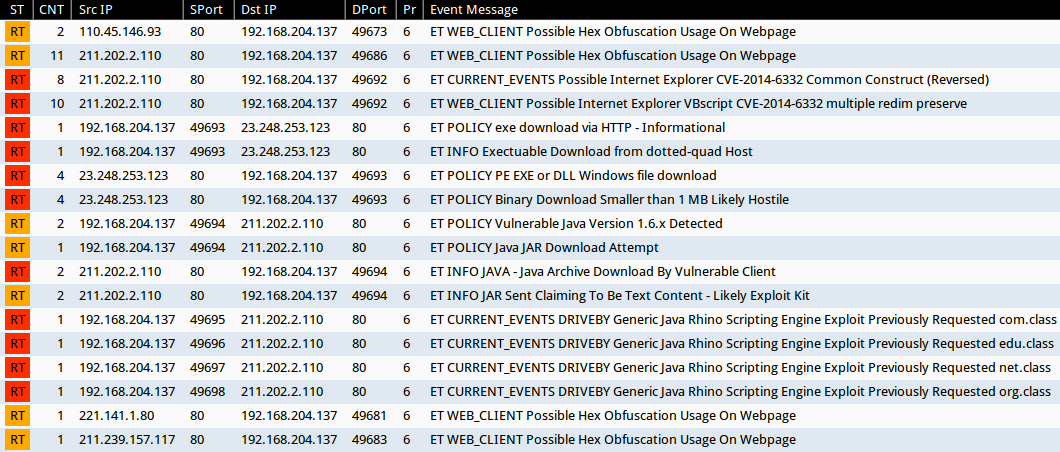
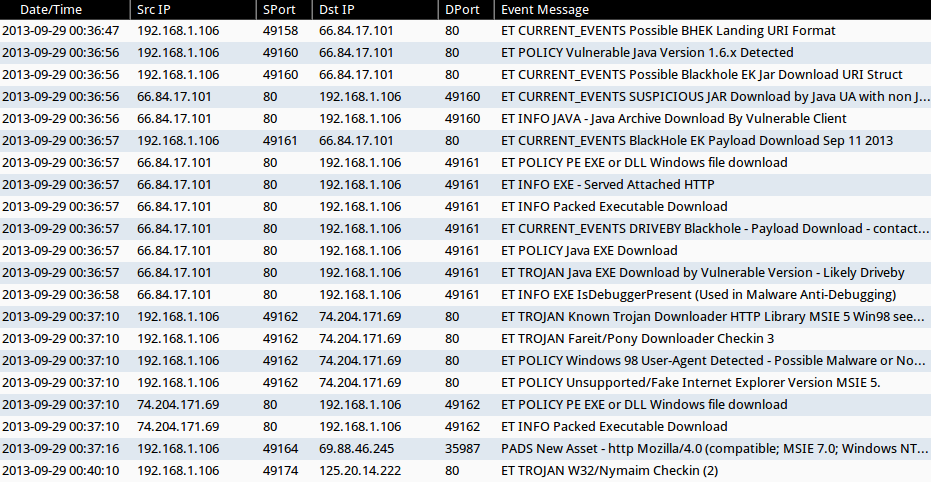
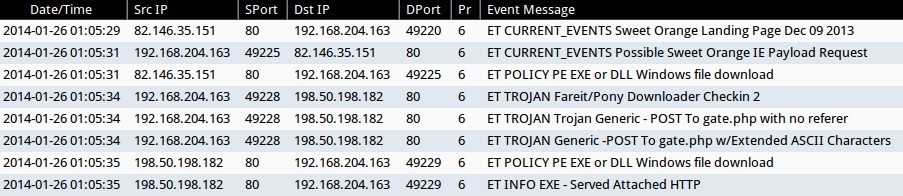
Brad on Twitter: "@Ledtech3 Rules those URLs trigger: - ET POLICY Binary Download Smaller than 1 MB Likely Hostile - ET POLICY PE EXE or DLL Windows file download HTTP - ET

Quick Malware Analysis: TA551 / SHATHAK / IcedID / BOKBOT pcap from 2022-01-06 · Security-Onion-Solutions securityonion · Discussion #6842 · GitHub

Quick Malware Analysis: malware-traffic-analysis.net pcaps from 2021-06-02 · Security-Onion-Solutions securityonion · Discussion #5045 · GitHub