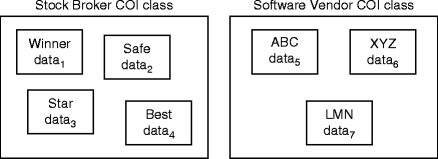
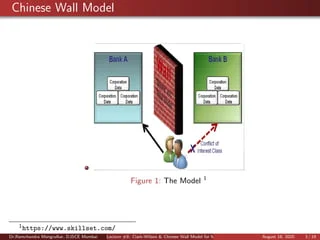
Week 8 - Friday. What did we talk about last time? Bell-La Padula model Clark-Wilson model Chinese Wall model Biba model. - ppt download
EVALUATION OF THE APPROPRIATENESS OF TRUST MODELS TO SPECIFY DEFENSIVE COMPUTER SECURITY ARCHITECTURES FOR PHYSICAL PROTECTION


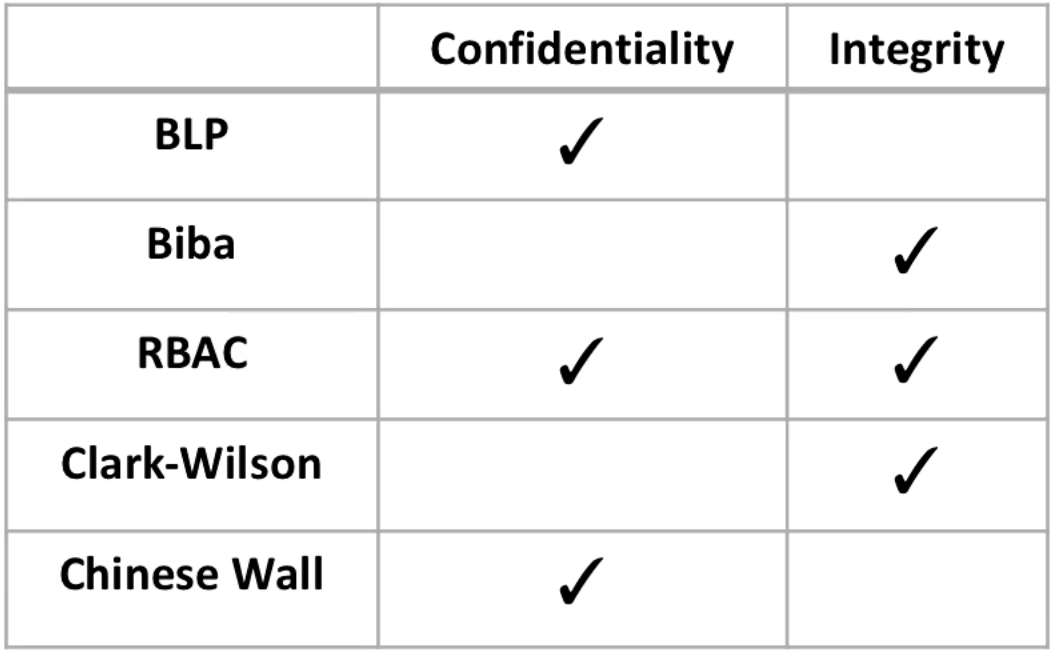
![PDF] Study of Access Control Models | Semantic Scholar PDF] Study of Access Control Models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7c6c6a84d6c05dfdf337296cdb9953131fa8122d/4-TableII-1.png)