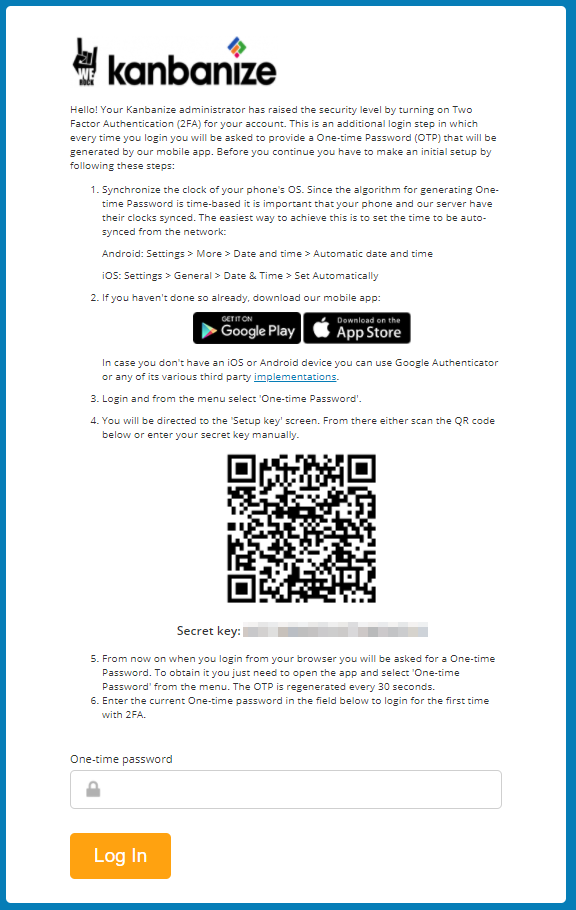
Authenticate Application Access Ppt Inspiration Backgrounds Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

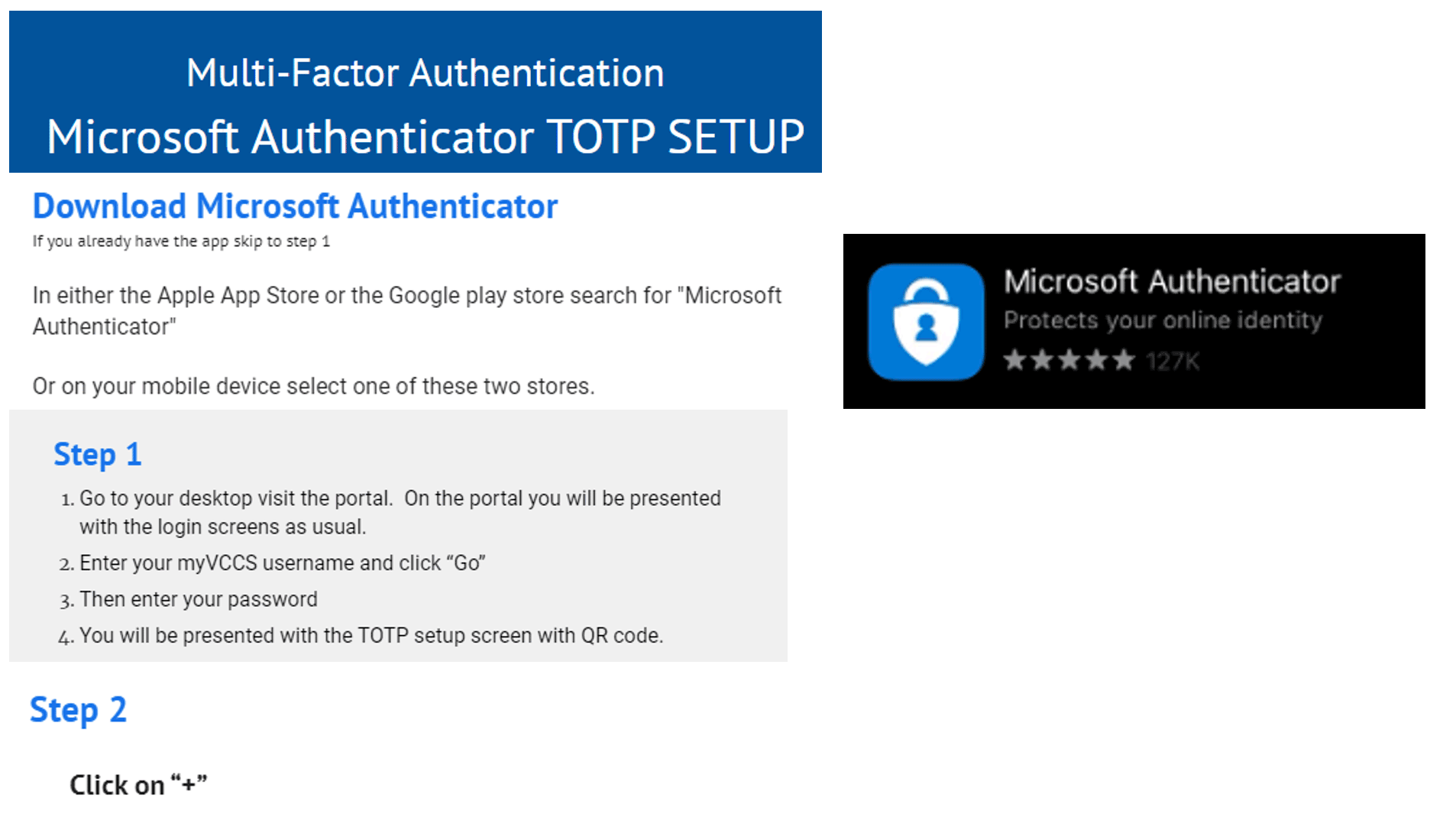
SAP Cloud Platform API Management authentication using SAP Cloud Platform Identity Authentication Service | SAP Blogs
![PDF] Authentication Process between RFID tag and Mobile Agent Under U-healthcare System | Semantic Scholar PDF] Authentication Process between RFID tag and Mobile Agent Under U-healthcare System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/08fb906f4ca9fd9f52e8b757eace7226d1fa23f8/4-Figure1-1.png)